Early-Stage Security Trap: Overpowered Access
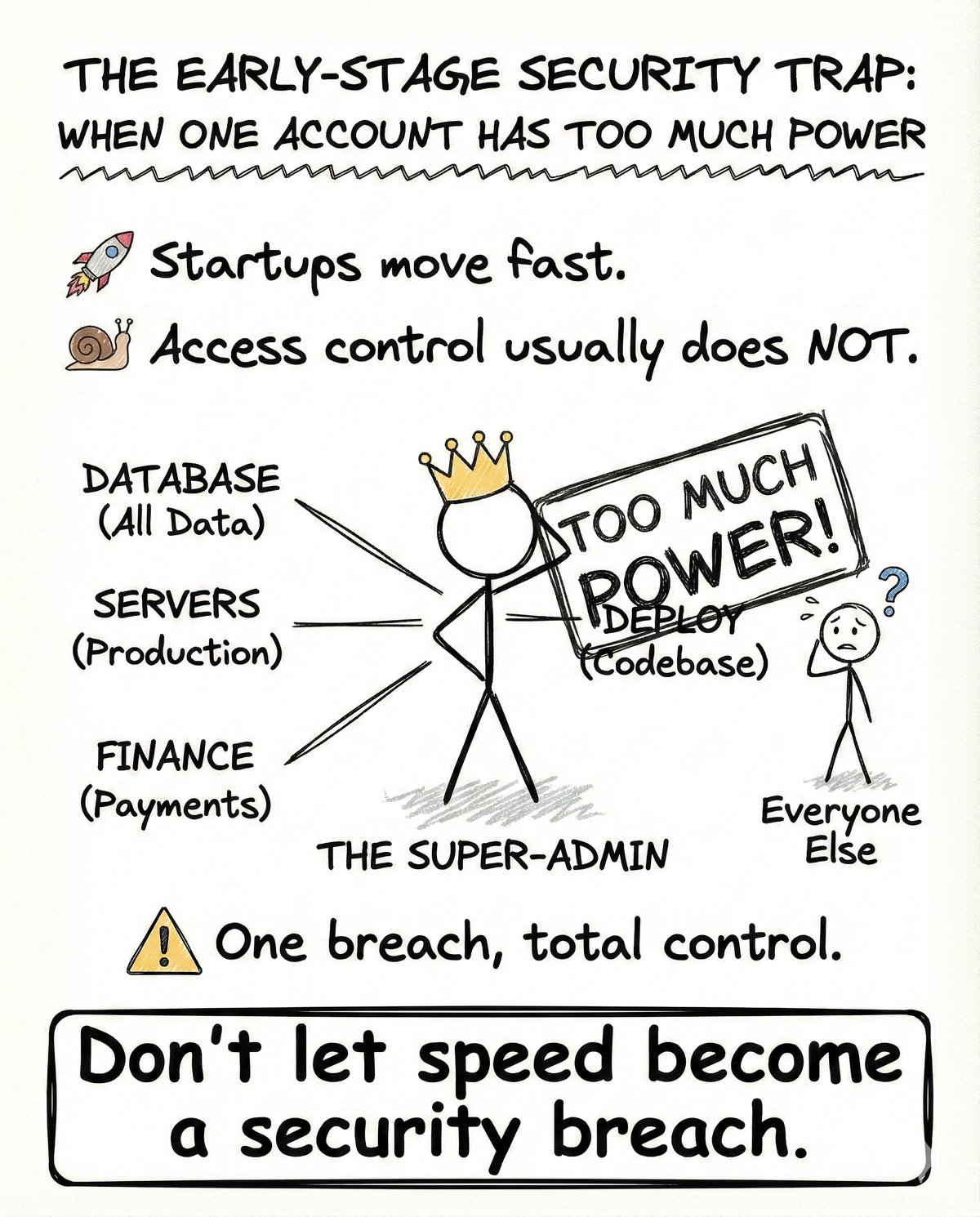
When one account has too much power
Startups move fast.
Access control rarely keeps up.
That gap is where most early-stage security failures begin.
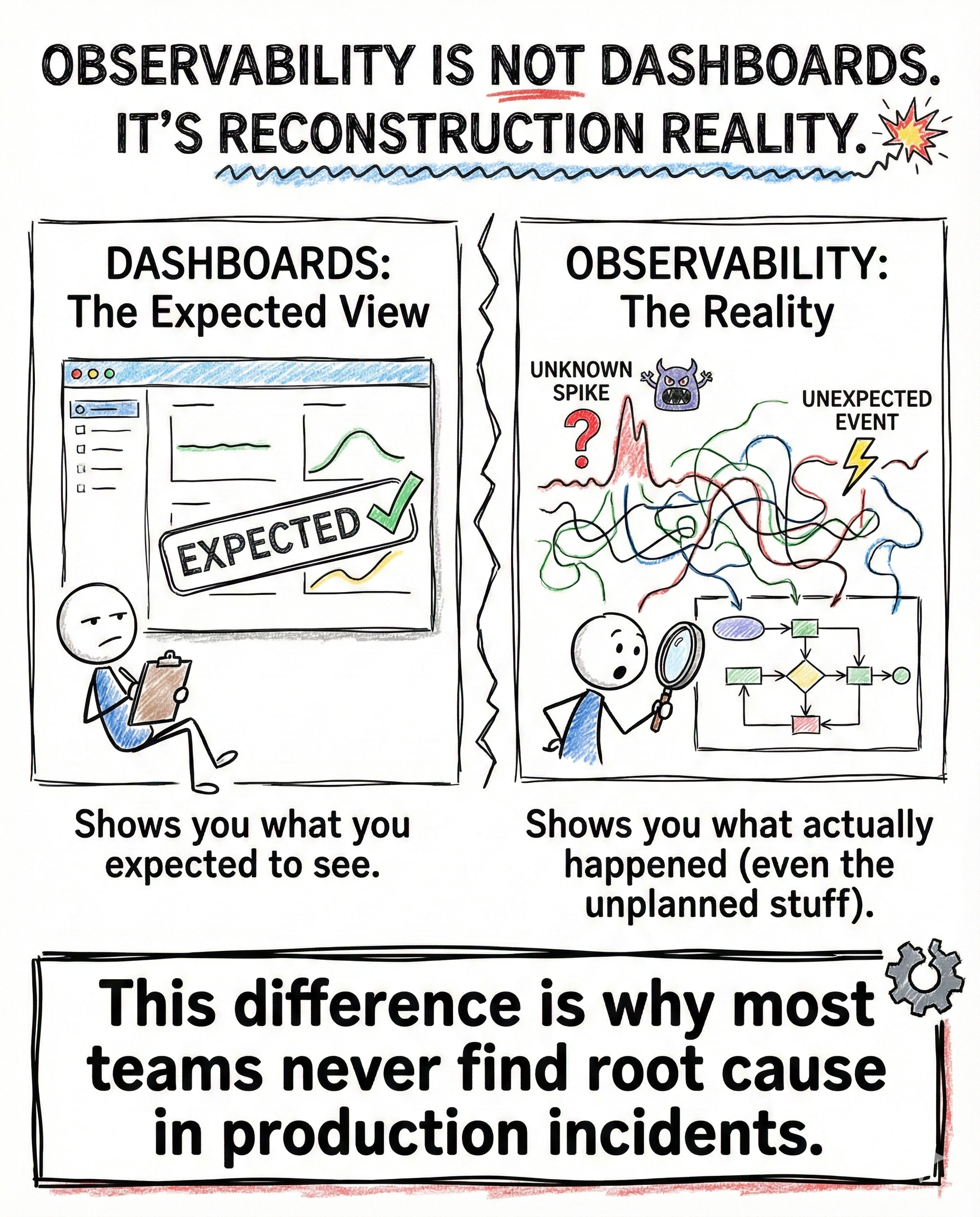
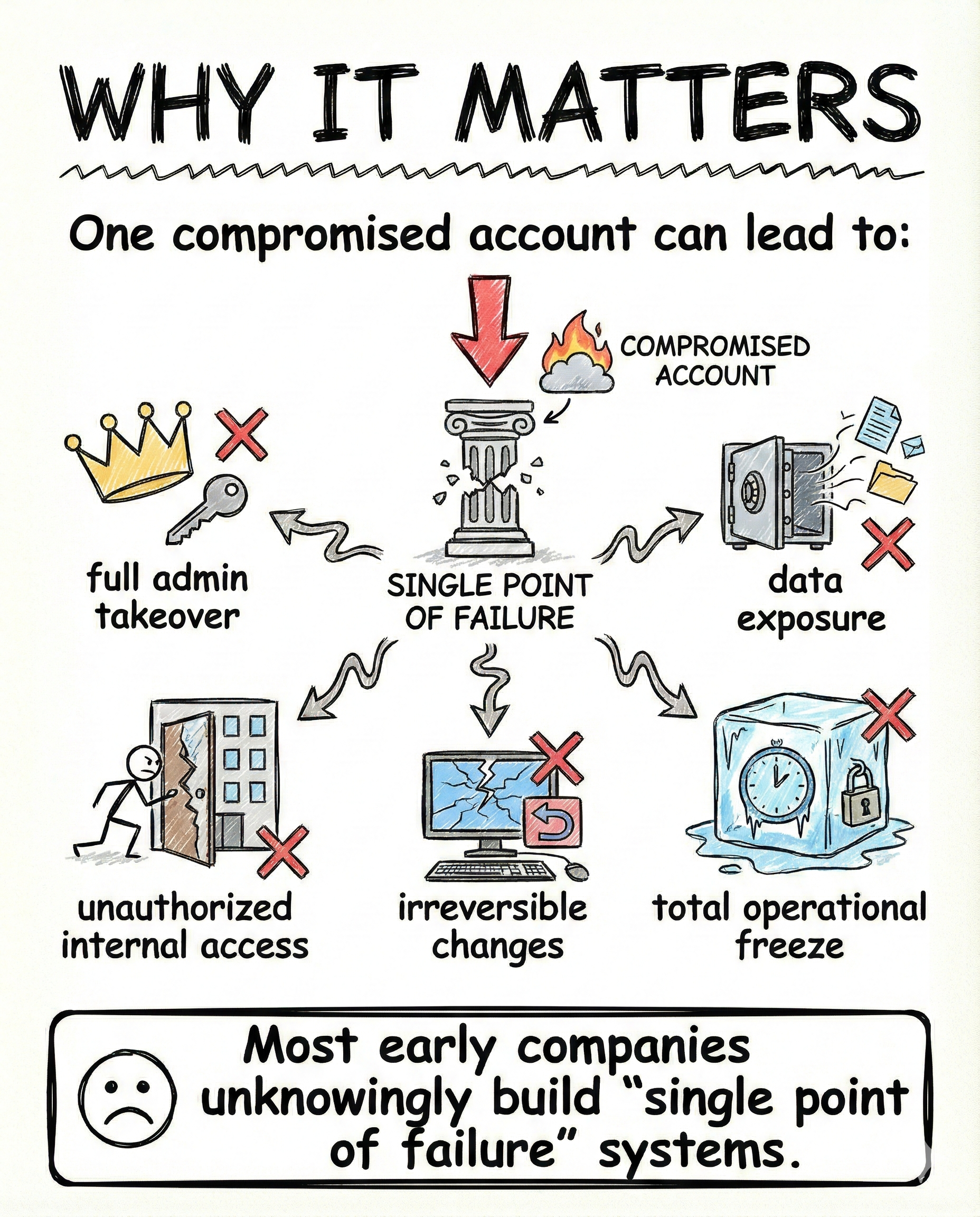
Why this matters more than people think
One compromised account is often enough.
The damage can include:
- full admin takeover
- sensitive data exposure
- unauthorized internal access
- irreversible configuration changes
- complete operational freeze
Many early companies unknowingly build systems with a single point of failure.
They only realize it after something goes wrong.
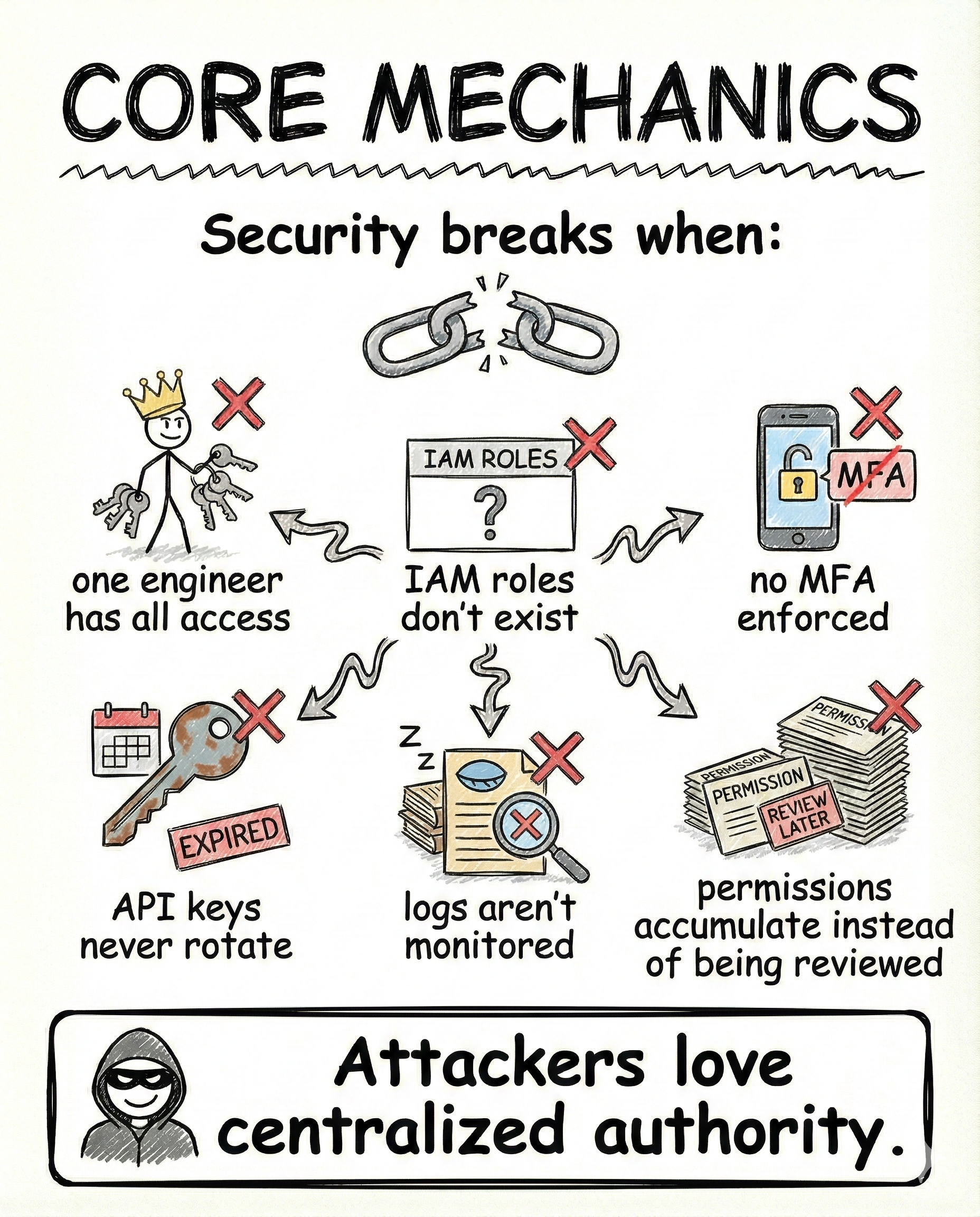
How access quietly becomes dangerous
Security usually breaks through accumulation, not intent.
Common failure patterns:
- one engineer holding full access everywhere
- no real IAM roles
- MFA not enforced consistently
- API keys that never rotate
- logs that no one watches
- permissions added but never reviewed
Attackers do not need sophistication when authority is centralized.
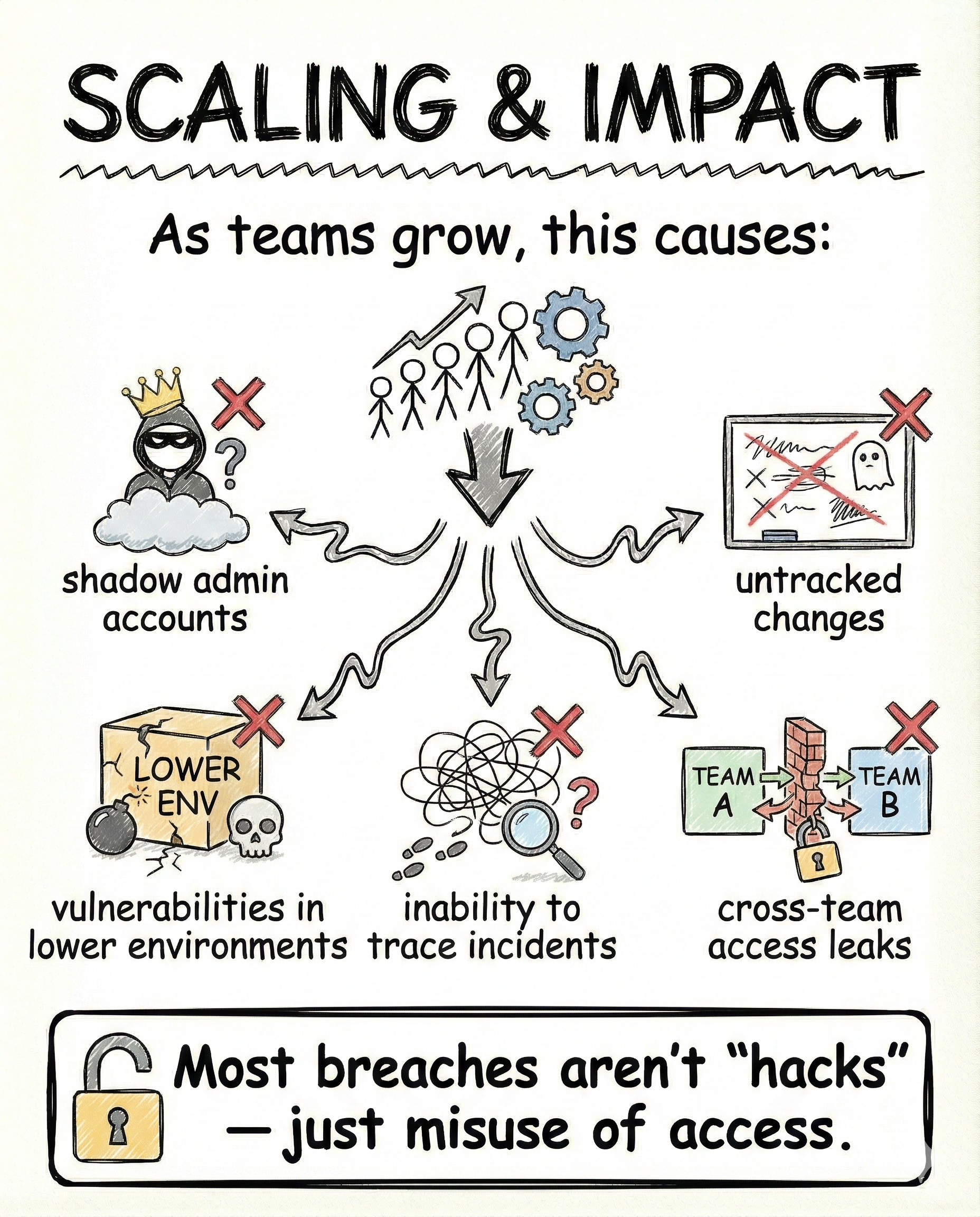
What happens as teams grow
The problem compounds with scale.
You start seeing:
- shadow admin accounts
- changes with no clear owner
- weak lower environments that leak upward
- incidents that cannot be traced
- access bleeding across teams
Most breaches are not clever hacks.
They are misuse of existing access.
Lessons from real environments
These rules exist because things broke without them:
- enforce least privilege from day one
- use IAM roles instead of long-lived keys
- separate development, staging, and production
- rotate secrets regularly
- monitor logins from unknown ASNs
- never depend on a single admin account
Security is not paranoia.
It is architectural discipline.
The real takeaway
Access control is invisible when it works.
When it fails, everything stops.
Fixing it early is cheap.
Fixing it after growth is painful.

Closing
This post is part of InsideTheStack, focused on preventive engineering lessons that avoid incidents before they exist.
Follow along for more.
#InsideTheStack #SecurityArchitecture #IAM